Hash Function Is One Type of Computer Security That Provides Authentication & Data Integrity – A Quick Guide on Hash Function and How Does It Work
Cryptography is the essential process and method that’s used for maintaining the integrity, confidentiality, and security of the data. It’s essential to create robust machine identities that protect machine-to-machine communications and connections. Put simply, the hash function is the mathematical process that has an essential part in public-key cryptography.
In addition, the hash function helps in:
- Store password in database securely
- Authenticates securely
- Organizes files & content efficiently
- Assurance of data integrity by giving indication whenever data is altered
Furthermore, hash functions are helpful in many other ways. For instance, it helps sign software applications and secure the website connection to transmit information online.
What is Hash Function?
The hash function is seen differently by different people. But it becomes a bit different if you’re questioning what a hash function in cryptography is. The hash function is seen as a unique identifier for any content in cryptography. It processes the plaintext data of all sizes and converts it into a unique ciphertext of a certain length.
In other words, hashing is a mathematical function that gives an output called a hash value of ciphertext or plaintext. It’s a cryptographic technique that transforms your data into a specific text string. Henceforth, once you put a plaintext within a strong hash algorithm, you get the output in a hash value.
Similarly, the hash function is a one-way cryptographic algorithm that maps your input of all sizes to a unique output of a fixed length in bits. The resulting output is known as a hash value, hash digest, or hash code, which is the resulting unique output.
How Does Hash Function Work?
Hashing converts readable text into unreadable text, making it secure. And, once hashing is executed, it’s not easy to reverse, which makes it a little different from encryption, where you can reverse the encrypted information.
The original data input is often broken down into small blocks of equal sizes in hashing methods. And, if there’s not enough data within any block to make it of the same size, padding (1s and 0s) is added. Similarly, those individual data blocks are run using a hashing algorithm and give an output known as a hash value.
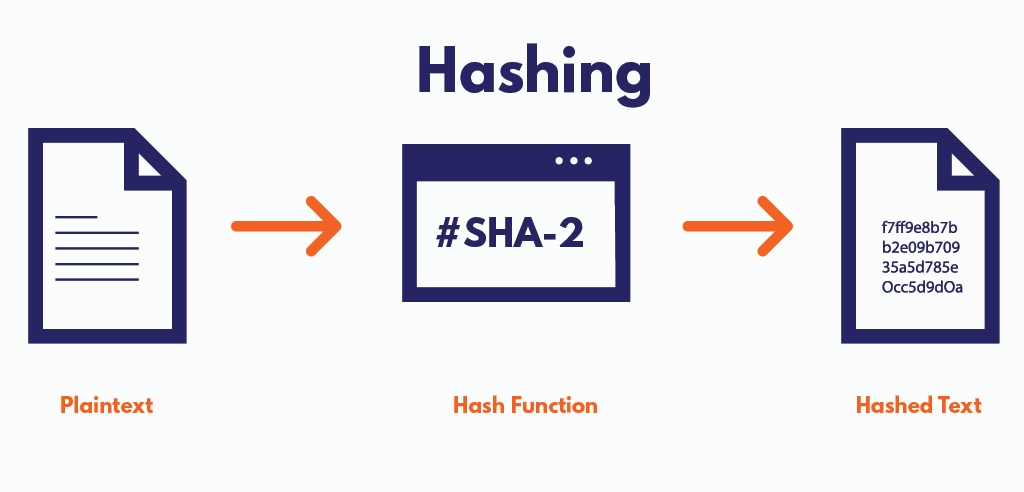
No doubt, the process may differ if you’re hashing passwords for storing in a web server. But, the hashing of passwords for storing involves salting. Salt is a unique random value added to the message before it undergoes the hashing algorithm. Lastly, adding one character will create a new hash value once the process is completed.
Hash Function vs. Encryption
No, They Aren’t the Same
Though both hash function and encryption use cryptography, they are not similar. For instance, a hash function is a one-way function, meaning you can’t reverse once you covert readable content into ciphertext. And, when it comes to encryption, you can convert it back into a readable format, also known as decrypting, after it’s encrypted. But it would help if you were authorized to decrypt the encrypted information.
Similarly, hashing is mainly used for comparison reasons and not for encryption.
| Feature | Hash Function | Encryption |
|---|---|---|
| Goal | One-way transformation of data | Reversible transformation of data |
| Use Case | Verify data integrity, fingerprints, message digests | Protect confidentiality of data |
| Input | Any data of arbitrary length | Plaintext data |
| Output | Fixed length hash value | Ciphertext of same or variable length |
| Key Usage | Optional secret key | Required secret key |
| Security | Resistant to preimage and collision attacks | Resistant to cryptanalysis attacks |
| Operation | Not reversible, hash can’t be decrypted | Encryption is two-way, ciphertext can be decrypted |
| Examples | MD5, SHA-1, SHA-256, SHA-512 | AES, RSA, Blowfish, RC4 |
Common Strong Hash Algorithm
Some of the most commonly used hashing algorithms are:
- MD4
- MD5
- RIPEMD
- SHA
- TIGER
- WHIRLPOOL
Properties of Hash Function
Below are the properties of the Hash Function:
- Deterministic: Output will not differ. And the hash value will be the same.
- Not Reversible: The hash function is not reversible. Henceforth, once the hash value is generated, it’s impossible to reverse it.
- Collision Resistant: Two inputs will never have a similar output.
- Non-Predictable: A hash function randomly generates its hash value. So, each time a unique hash value is generated, you can’t predict what it’ll be.
- Compression: The hash function produces a compressed hash value. It means the output size is much smaller than the input size.
Applications of Hash Function
Storing Passwords
Hashing secures passwords that are stored and saved on the server. Instead of storing passwords in plaintext, you store actual hash values within the hash table by hashing. Therefore, if an intruder tries to log into the system, they can only see the hash value and not the actual passwords.
Verification of Passwords
Hashing is useful for verifying passwords every time you log into your account or system. Password verification shows you’re the actual user of the account. Similarly, if your password matches the hash value on the server, it confirms you’re authorized.
The Integrity of the Data
Hashing verifies data integrity. It assures you that your data is not modified and it’s correct. Similarly, it also ensures your information is in its original form.
Common Uses of Hash Function
Hash functions are helpful for most things. For instance, it’s used to sign new software and verify digital signatures to secure the website connection with the computer or mobile web browsers. Similarly, it’s also good for indexing and retrieving information from the online database.
For instance, the hash function is commonly seen in usage for:
- Data blocks within cryptocurrencies
- Blockchain technologies
- For storing passwords in an online database. (Though, it requires a little dash to make hashing more secure.)
In addition, the hash function is commonly found through public-key cryptography. For example, the hash function is seen in:
- SSL/TLS certificate
- Code Signing certificate
- Email Signing certificate
- Document Signing certificate
- Used for comparing and preventing duplication within the database
- Used widely in computer graphics
- Used for finding specific data from the big database
Example of Hashing
For instance, you are looking to digitally sign software and distribute it online on your website for download. For this, you’ll need to create a hash of the executable you’re signing. After embedding your digital signature, you’ll need to hash that digital signature.
Once the user downloads that software, the browser goes to decrypt the file, and at that time, it inspects the two unique hash values. Similarly, the browser will run the same hash function with the help of the same used algorithm and hash both the signature and file once again. If the produced hash value is the same, the browser knows that both the file and signature are authentic and not altered. If the hash value differs, the browser will show a warning message.
Wrapping Up
Hashing is an essential tool for computer security. It helps secure data and offers visibility within the alteration or modification of files and data. In addition, its unique characteristics prevent attackers from taking advantage of reverse engineering for viewing plaintext or original input data.
Lastly, in combination with other cryptographic tools like encryption, the hash function supports authentication, signatory non-repudiation, and data integrity when using digital signatures.
Expert in Software & Web App Engineering
Parag Mehta, the CEO and Founder of Positiwise Software Pvt Ltd has extensive knowledge of the development niche. He is implementing custom strategies to craft highly-appealing and robust applications for its clients and supporting employees to grow and ace the tasks. He is a consistent learner and always provides the best-in-quality solutions, accelerating productivity.
![What Is a Hash Function Within Cryptography [Quick Guide]](https://positiwise.com/blog/wp-content/uploads/2022/06/hash-function-guide-1.jpg)


